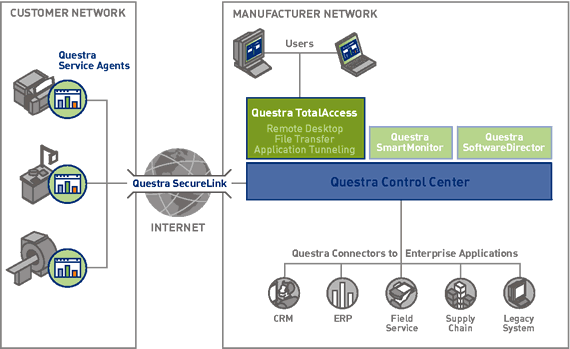
Suited to environments demanding rapid response and problem resolution, the Questra TotalAccess™ application provides secure, audited remote access over the Internet to devices deployed at customer sites. This secure "anytime, anywhere" access features remote desktop control, file transfer, and application tunneling capabilities that let you run existing diagnostic tools remotely. The result is fewer on-site service visits, shorter problem resolution times, and reduced overall service costs.

Type topic text here.
Questra TotalAccess enables remote service personnel to view, troubleshoot, diagnose, and solve problems on a device as if they were on location at the customer's site.
Complete remote access capabilities - This capability features three remote access capabilities to enhance an organization's services offering and drive down costs.
Remote desktop - Enables service personnel to view and modify device settings from any location with Internet access. Remote desktop can also streamline telephone support processes by reducing an organization's dependence on customers to identify and explain symptoms. Problem resolution times and costs can be dramatically reduced by initiating remote "site visits" that either eliminate onsite visits altogether or reduce their length by ensuring a technician arrives with a correct diagnosis and replacement parts.
File transfer - Permits the transfer of files for troubleshooting, thus eliminating dependence on customers to send log files or other diagnostic information to a business's support center.
Application tunneling (via serial port, IP, and telnet emulation) - Gives the ultimate in flexibility. Field service technicians don't need to be on site to run their diagnostic applications. Rather, they can deploy proprietary diagnostics tools over a secure Internet connection, thus maintaining compliance with existing support processes and leveraging an organization's investment in existing tools.
Customer control over remote desktop permissions - This capability supports features that allow end customers control over access by remote service personnel.
Customer must explicitly initiate, allow, or deny access, and can terminate a connection at any time.
An audit trail of network access attempts is visible to customers.